Implementation Guide: FortiGate SSL VPN with Okta MFA using SAML
- Matt Sherif

- Mar 20, 2022
- 4 min read
You may be wondering didn't you already post a redirect to Kim Frellsen's blog on this? Yes, yes I did. Here's the thing though, I came across someone asking a question about certain behavior so I decided to go through this and document the process based on my own experience with SAML.
Assumptions:
FortiGate running FortiOS 6.4.0 or higher. This guide was written on FortiOS 7.0.5
Paid FortiClient, FortiClient Cloud or FortiClientVPN 6.4.x or higher
Your own deployed Okta instance
Not required - however I find that life is easier with it - a publicly trusted cert in the FQDN name of your VPN portal (This is required if you want to do single log out)
With that out of the way let's get to the good stuff!
Setting up Identity Provider (IdP) on Okta
The first step in this process is to set up our SAML IdP, this is unique to your chosen SAML platform. Here's what's needed to set it up in Okta:
From the Okta Admin dashboard go to Applications > Applications > Click on Create App Integration
In the "Create a new app integration" menu click on "SAML 2.0"
In "General Settings" configure a meaningful name, app logo (optional), and choose app visibility and click next
In the "Configure SAML" page set the following values
These values are configured based on the assumption you already know the VPN FQDN (e.g. vpn.fqdn.com) and port. For this demonstration I will be using the default HTTPS port
Single Sign-on URL: this is your https://vpn.fqdn.com:port/remote/saml/login/ URL - you can omit the port if you're using the default HTTPS port (443)
Audience URI (SP Entity ID): This is what the FortiGate refers to as the metadata URI or entity-id, and should look like this http://vpn.fqdn.com:port/remote/saml/metadata/
Default RelayState: we don't use this on FortiGate
Name ID format: Select "Unspecified"
Application username: Select the attribute you wish to specify as the username, for this writing I will be using the "Email" attribute
Optionally you can click on "Show Advanced Settings" to configure Single Logout
Single Logout URL: https://vpn.fqdn.com/remote/saml/logout/
SP Issuer: this is the FortiGate entity-id https://vpn.fqdn.com/remote/saml/metadata/
Signature Certificate: use the same Certificate you used for the vpn login page
Note on 7.0.5 I get a "some unknown error!" on single log out, thought it seems I log out correctly

Single logout settings:

Attribute Statements: set the value as such:
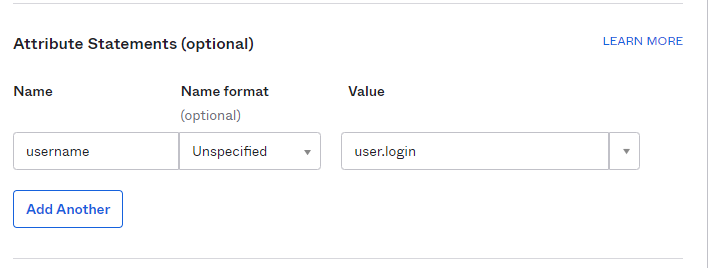
Click next
In the "Feedback Section" - set the value of "are you a customer or a partner?" select "I'm an Okta customer adding an internal app"
Click Finish
You'll be redirected to the application we just created, in that you will see a section called SAML 2.0:

Click "View Setup Instructions"
Note the values of the following:
Identity Provider Single Sign-On URL: this will map to the FortiGate Assertion Consumer Service URL (idp-single-sign-on-url in CLI)
Identity Provider Issuer: this will be the Entity ID (idp-entity-id) on the FortiGate
Click 'Download Certificate'

Assigning the application to users:
In order to authenticate to the FortiGate, we need to ensure the "Application" we just created is accessible by the users we intend to allow VPN access to. Click on the "Assignments" tab from the Application Dashboard and assign the users you wish to assign access to - in this example I assigned "SSL_VPN_USERS" to the application:

Importing Okta Certificate to FortiGate:
We will import the certificate we downloaded in the last section into the FortiGate, and we will use it as the certificate for the Okta IdP we configure on the FortiGate side:
Browse to System > Certificates (if you don't see this option enable Certificates from System > Feature Visibility)
Click on "Create/Import"
Select "Remote Certificate"
Click on "+Upload" - and upload the certificate we downloaded in the previous section
Click OK
Find your certificate in the UI - it will be named something like "REMOTE_Cert_X"
Optional - rename the cert to something more meaningful
From the CLI enter the following:
config vpn certificate remote
rename REMOTE_Cert_X to okta.saml.cert
endNow we're ready to set up the FortiGate as a Service Provider
Setting up the FortiGate as Service Provider (SP)
How to do this in the UI:
Go to User & Authentication > Single Sign-On
Click on Create New
Give the Service Provider a meaningful name, in my case I chose Okta.users (real creative, I know)
For the address, specify the FQDN (e.g. vpn.mydomain.com)
If you're using 7.0.5 you will need to make some adjustments to the auto generated URLs in the CLI, as I have confirmation from Fortinet that these were changed unintentionally. Refer to the CLI portion below

Specify the certificate you wish to use - this is optional, I like to use it, but it's totally up to you
Click next
In identity provider details click type custom
Entity ID: this is the Idenity Provider Issuer we noted from Okta
Assertion consumer service URL: the Identity Provider Single Sign-On URL from Okta
Single logout service URL: https://<your_okta_domain>.okta.com
Certificate: the Okta cert we imported in the previous section
Attribute used to identify users: username
Click "Submit"

The same steps above in the CLI:
config user saml
edit "Okta.users"
set cert "vpn.fqdn.com.crt"
set entity-id "http://vpn.fqdn.com/remote/saml/metadata/"
set single-sign-on-url "https://vpn.fqdn.com/remote/saml/login/"
set single-logout-url "https://vpn.fqdn.com/remote/saml/logout/"
set idp-entity-id <Okta Identity Provider Issuer>
set idp-single-sign-on-url <Okta Identity Provider Single Sign-On URL"
set idp-single-logout-url "<Okta Single Logout URL>"
set idp-cert "okta.saml.cert"
set user-name "username"
set digest-method sha256
next
endNote that the digest-method may need to be set even if you created this from the UI.
Map the SAML IdP to a user group:
Now that we created the SAML configuration, we need to map it to a group so we can use it:
Navigate to User & Authentication > User Groups
Click "+Create New"
Give the group a meaningful name
Click "+Add" under "Remote Groups"
Select the Okta IdP you created
Click OK
Click OK

Because I am also using ADFS, Azure-AD and other SAML IdPs I will need to create an SSL VPN Realm and assign it an FQDN. If you're not using any other SAML IdPs you can skip these steps.
After you've created the Realm you will need to create a mapping to it in VPN > SSL-VPN Settings:

Last but not least, don't forget to add the group to your SSL-VPN policies.
Testing access - web mode:
Testing access - tunnel mode:
Thanks for reading, I hope this is helpful.
Madman out!




Comments